In this Post I will show you how to Publish all of the Exchange Services in Firewall Rules (with certificates) so you can access it through Webmail, ActiveSync and/or Outlook Anywhere.
This will work with Microsoft Exchange 2007/2010 and Microsoft ISA 2006 and TMG 2010. Other versions of Exchange will work, but you will need to change some of the paths in the Firewall.
The Steps are:
- Create and Import the Certificates;
- Configure the Exchange Server;
- Create the Web Listener in the Firewall;
- Configure of the Publishing Rules
- WebMail (OWA)
- Outlook Anywhere
- ActiveSync
- Troubleshooting
So, let's begin!
1. Create and Import the Certificates
- Create a new certificate request in the Exchange Management Shell
Result
Thumbprint Services Subject 978200E549A8E7B150879BA96B996DAF1B38D847 ..... CN=owa.lab.com, O=LAB...
NOTE: The first SAN name must be equal to the Common Name (in red)
- Get the Certificate
https://technet.microsoft.com/en-us/library/cc731183(v=ws.11).aspx
Now, if you open the browser and change the address to http://CA-SERVER-NAME/certsrv you can request a new certificate:
Click in Request a Certificate and then in Advanced certificate request choose "Certificate request by using a base-64-encoded CMC or PKCS #10 file or submit a renewal request by using a base-64-encoded PKCS #7 file".
Open the request file created with the powershell command c:\mailcertrequest-25052016.req, select everything (CTRL + A) and copy paste into the form. Select the Web Server Template:
Submit the Request and Choose the option "Download Certificate" (ex: C:\new_cert.cer).
Now go back to the Exchange Powershell and import the newly created certificate with the command:
Import-ExchangeCertificate -path c:\new_cert.cer
Result
Thumbprint Services Subject ---------- -------- ------ A547C648A75B141BFBCD1E7D4FE23A0F6FC06149 ..... CN=owa.lab.com, O=LAB...
Validate the certificate thumbprint:
Dir cert:\LocalMachine\My | fl
Result
CN=owa.lab.com, O=LAB, DC=com, DC=lab Issuer : CN=lab-ca, DC=lab, DC=lab Thumbprint : A547C648A75B141BFBCD1E7D4FE23A0F6FC06149 FriendlyName : Microsoft Exchange 2007 NotBefore : 04-12-2007 13:14:04 NotAfter : 03-12-2009 13:14:04 Extensions : {System.Security.Cryptography.Oid, System.Security.Cryptography. Oid, System.Security.Cryptography.Oid, System.Security.Cryptogra phy.Oid, System.Security.Cryptography.Oid, System.Security.Crypt ography.Oid, System.Security.Cryptography.Oid, System.Security.C ryptography.Oid}
Connect the certificate with the Exchange Services:
Enable-ExchangeCertificate -thumbprint A547C648A75B141BFBCD1E7D4FE23A0F6FC06149 -services "IIS,SMTP,POP,IMAP"
2. Configure the Exchange Server
1. Define the Internal and External OWA Addresses:
After that, perform a "iisreset /force" in the command prompt.
Activate the Outlook Anywhere feature using the external name and NTLM authentication mode:
On the MMC console, open the certificates snapin choosing the Local Computer Account (Exchange Server).
Click on the certificate and export:
Click Yes on the export the private Key, choose a password and save the PFX file.
For more information follow this guide:
https://technet.microsoft.com/en-us/library/cc754329(v=ws.11).aspx
Install the "RPC over HTTP Proxy" in the CAS Server. Restart and check if all the services are all up and running.
3. Create the Web Listener in the Firewall
Open the ISA/TMG Server and select "View System Policy Rules" in "Firewall Policy". Click with the right mouse button in the policy "Allow all HTTP traffic from ISA Server to all network (for CRL downloads)" and select "Edit System Policy". Confirm that the red arrow point to "CRL Download" and choose the option "Enable this configuration group". Apply the changes:
Import the PFX Certificate on the ISA/TMG Server. On the mmc console, open the certificates snapin choosing the Local Computer Account (ISA/TMG Server). Click on Personal -> Certificates and choose Import:
Click Next and then browse to the PFX Certificate (you might need to change the browse extensions to find all them, like *.*). Type the same password when you exported and Finish the process. On the snapin you must have the certificate with the private key (the icon must appear with a yellow key).
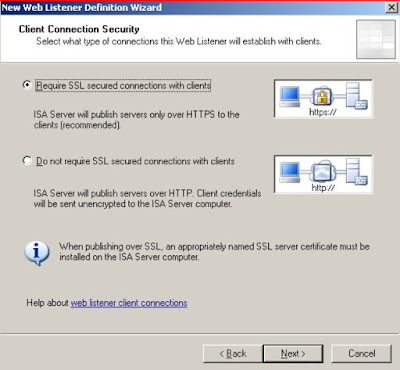
Create the WebListener on the ISA/TMG Server going to Toolbox -> Web Listener -> New Web Listener and give it a Name like SSL:
Choose the "Require SSL..." Option:
Select the Internal and External network (you must have an External IP Address free for all the Exchange Services Publications on port 443):
In the Internal Network pick "Select IP Addresses" and choose the Internal IP:
Do the same for the External IP Address (you can reuse an IP Address if the port 443 isn't being used):
Assing the previous certificate to both IP Addresses (I'm assuming that one IP is for external access and the other is for internal access with routing):
4. Configure the Publishing Rules
- Webmail BASIC (OWA - Outlook Web Access)
It will work with Exchange 2007 and 2010 (choose the correct version and OWA):
Our Publishing Rules will use Certificates, so choose SSL:
Enter the internal name (the internal DNS name that the Users/Clients will access to Email) and the Internal Exchange Server name or IP Address:
Enter the external name (the external DNS name that the Users/Clients will access to Email). It must be the same as the internal name, because our certificate only have one DNS Name. If you have a Wildcard Certificate, you can use a different external name:
Choose the Web Listener that we created earlier:
Choose Basic Authentication (the next rule is equal to this one, but will use NTLM):
Finish the Wizard and open the proprieties. Remove "owa" from the paths:
This Rule is now completed.
- Webmail NTLM (OWA - Outlook Web Access)
This Rule is now completed.
- Outlook Anywhere
It will work with Exchange 2007 and 2010 (choose the correct version and Outlook Anywhere):
Our Publishing Rules will use Certificates, so choose SSL:
Enter the internal name (the internal DNS name that the Users/Clients will access to Email) and the Internal Exchange Server name or IP Address:
Enter the external name (the external DNS name that the Users/Clients will access to Email). It must be the same as the internal name, because our certificate only have one DNS Name. If you have a Wildcard Certificate, you can use a different external name:
Choose the same Web Listener that we created earlier:
Choose NTLM Authentication:
Finish the Wizard and this Rule is Completed.
- ActiveSync
It will work with Exchange 2007 and 2010 (choose the correct version and ActiveSync):
Our Publishing Rules will use Certificates, so choose SSL:
Enter the internal name (the internal DNS name that the Users/Clients will access to Email) and the Internal Exchange Server name or IP Address:
Enter the external name (the external DNS name that the Users/Clients will access to Email). It must be the same as the internal name, because our certificate only have one DNS Name. If you have a Wildcard Certificate, you can use a different external name:
Choose the Web Listener that we created earlier:
Choose Basic Authentication:
Finish the Wizard and all the rules are now completed.
This will work without a certificate warning if all the clients are in the domain. If not, you must export the CA Root Certificate and Import it in all the machines. Let's see an example of how to do this:
Go back to the Exchange Server and open the IIS Console. Open the "Default Web Site" proprieties, select "Directory Security" and "View Certificate":
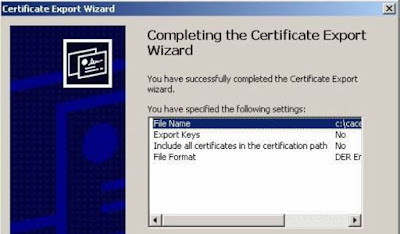
Select "Certification Path” and in the Upper level, select the Certificate Authority and click "View Certificate". Select the "Details" tab and "Copy to File". In the Wizard select the following options:
The path to export the ROOT certificate:
Finish to Complete:
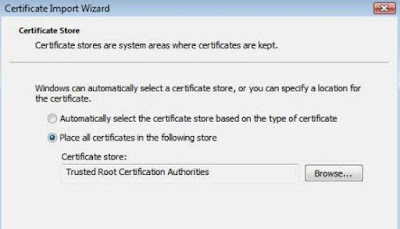
This certificate is only required in clients that are not in Domain (the others already have it, i Hope!). Let's see how to install this exported certificate in the Machines. Open MMC and add the certificate snapin for "Computer Account", Local Computer:
In "Trusted Root Certification Authorities", select "Certificates" and right click in "Certificates", "All Tasks" and choose "Import". Select the previously exported certificate (*.cer):
The next image is an example of the Outlook Anywhere configurations in an Outlook client look like. You can customize some options manually or by GPO (Group Policy):
5. Troubleshooting
All publishing scenario described above presupposes the existence of a split-dns type setting. For that, it means that the internal machines resolve the owa.lab.com name to the IP address of the CAS server (forward lookup zone created in the internal DNS), while customers in the Internet resolve the owa.lab.com to the public IP address CAS server (forward lookup zone on an external DNS).
You can configure the Internal and External paths of all the WebServices in powershell:
Set-ClientAccessServer -Identity lab-e2k7.lab.local -AutodiscoverServiceInternalUri https://owa.lab.com/autodiscover/autodiscover.xml
Set-WebServicesVirtualDirectory -Identity "lab-e2k7.lab.local\EWS (Default Web Site)" -InternalUrl https://owa.lab.com/ews/exchange.asmx
Set-OABVirtualDirectory -Identity "lab-e2k7.lab.local\oab (Default Web Site)" -InternalUrl https://owa.lab.com/oab
Set-UMVirtualDirectory -Identity "lab-e2k7.lab.local\unifiedmessaging (Default Web Site)" -InternalUrl https://owa.lab.com/unifiedmessaging/service.asmx
If you have the following error:
Warning message when you start Outlook 2007 and then connect to a mailbox that is hosted on an Exchange 2007-based server: "The name of the security certificate is invalid or does not match the name of the site"
Probably Cause:
- You replace the default self-signed Exchange 2007 certificate with a different certificate. Note The Exchange 2007 Setup program creates a default self-signed certificate when Exchange 2007 is installed.
- The common name on the replacement certificate does not match the fully qualified domain name (FQDN) of the URL that is stored in the following objects:
- The Service Connection Point object for the Autodiscover service
- The InternalUrl attribute of Exchange 2007 Web Service (EWS)
- The InternalUrl attribute of the Offline Address Book Web service
- The InternalUrl attribute of the Exchange unified messaging (UM) Web service
Resolution:
To resolve this issue, modify the URLs for the appropriate Exchange 2007/2010 components. To do this, follow these steps:
- Start the Exchange Management Shell.
- Modify the Autodiscover URL in the Service Connection Point. The Service Connection Point is stored in the Active Directory directory service. To modify this URL, type the following command, and then press ENTER: Set-ClientAccessServer -Identity CAS_Server_Name -AutodiscoverServiceInternalUri https://mail.contoso.com/autodiscover/autodiscover.xml
- Modify the InternalUrl attribute of the EWS. To do this, type the following command, and then press ENTER: Set-WebServicesVirtualDirectory -Identity "CAS_Server_Name\EWS (Default Web Site)" -InternalUrl https://mail.contoso.com/ews/exchange.asmx
- Modify the InternalUrl attribute for Web-based Offline Address Book distribution. To do this, type the following command, and then press ENTER: Set-OABVirtualDirectory -Identity "CAS_Server_name\oab (Default Web Site)" -InternalUrl https://mail.contoso.com/oab
- Modify the InternalUrl attribute of the UM Web service. To do this, type the following command, and then press ENTER: Set-UMVirtualDirectory -Identity "CAS_Server_Name\unifiedmessaging (Default Web Site)" -InternalUrl https://mail.contoso.com/unifiedmessaging/service.asmx
- Open the IIS manager.
- Expand the local computer, and then expand Application Pools.
- Right-click MSExchangeAutodiscoverAppPool, and then click Recycle.
- The original internal URLs for the Exchange components point to the internal FQDN of the server. For example, one of these URLs points to https://ServerName.contoso.com/ews/exchange.asmx.
- The FQDN that is specified on the certificate points to the externally accessible host name of the server. For example, the certificate specifies an FQDN, such as mail.contoso.com.
More Details in https://support.microsoft.com/en-us/kb/940726









































No comments:
Post a Comment